January 24, 2008

OnSecrity just released another video of the conversation we recorded last year during RSA. I am talking about security visualization in light of the book I am working on. This video cast is the sequel to the first one that I posted a few days ago.
 One of the topics I am discussing in the video is the “false dichotomy” between security and visualization. This is a topic that I talked about during a talk at the MIT Lincoln Labs at the beginning of December. The presentation showed how there are really two disciplines that come together in security visualization: Security and Visualization. The problem with this is that visualization people don’t know much about security and the other way around. It’s a very interesting topic to explore and it explains some of the mistakes that are being made with visualization tools and is also reflected in visualization research.
One of the topics I am discussing in the video is the “false dichotomy” between security and visualization. This is a topic that I talked about during a talk at the MIT Lincoln Labs at the beginning of December. The presentation showed how there are really two disciplines that come together in security visualization: Security and Visualization. The problem with this is that visualization people don’t know much about security and the other way around. It’s a very interesting topic to explore and it explains some of the mistakes that are being made with visualization tools and is also reflected in visualization research.
Technorati Tags: visualization, security, videocast
January 18, 2008
 It is pretty much exactly a year ago that I signed my contract with Addison Wesley to write a book about security data visualization. Now, a year later, I am getting really close. I am in the process of assembling my review committee and I a very excited about a couple of people that already accepted. Thanks in advance!
It is pretty much exactly a year ago that I signed my contract with Addison Wesley to write a book about security data visualization. Now, a year later, I am getting really close. I am in the process of assembling my review committee and I a very excited about a couple of people that already accepted. Thanks in advance!
There is still a lot to be done. I have one more big chapter to write: “Perimeter Threat” and a couple to finish up. But I can see the end! It’s nice to see the end being close!
A little more than a month after I signed my contract with my publisher, they recorded a video cast with me. I am talking about security visualization and a little bit about the book. Beware, this was a year ago. It is interesting, however, that I would probably still say about the same things! This shows that the market has not really changed much. I hope this will change soon though!
December 19, 2007
I just had a moment of awe. I was playing around with packet captures and was wondering whether Wireshark would still ship with a command line alternative for the GUI version. I always liked Ethereal for its protocol analysis capabilities. I pretty quickly found out that the command line version was still maintained. Now called tshark. I was sort of shocked, when I realized how much protocol traffic was actually decoded:
~/tmp$ sudo tshark -ni en1
Capturing on en1
2.004403 192.168.0.12 -> 207.46.27.163 MSNMS USR 1 YYYYYYY@hotmail.com 1452999922.70216123.6471199
3.672270 205.188.8.233 -> 192.168.0.12 AIM Buddylist Offgoing Buddy: ZZZZZZZZZZ
3.673979 205.188.7.244 -> 192.168.0.12 AIM Buddylist Offgoing Buddy: ZZZZZZZZZZ
5.136301 207.46.27.163 -> 192.168.0.12 MSNMS [TCP Retransmission] USR 1 OK YYYYY@hotmail.com Raffael%20Marty
5.136735 192.168.0.12 -> 207.46.27.163 MSNMS CAL 2 XXXXXX@hotmail.com
5.174140 207.46.27.163 -> 192.168.0.12 MSNMS CAL 2 RINGING 1111111111
6.750004 207.46.27.163 -> 192.168.0.12 MSNMS JOI XXXXXXX@hotmail.com XXXX%20Buding%20in%20boston
It understands the IM protocols (above version is anonymized)! I wonder how I could exploit this for some interesting visualization.
December 10, 2007
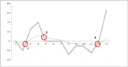 Today I found myself researching “moving average analysis” techniques. Using moving average analysis can be fairly useful in trending risk. Plot the moving average over your risk and compare it with the actual risk numbers, much like you would analyze a stock chart. I will write more extensively about this in my book in the “Visual Security Analysis” chapter.
Today I found myself researching “moving average analysis” techniques. Using moving average analysis can be fairly useful in trending risk. Plot the moving average over your risk and compare it with the actual risk numbers, much like you would analyze a stock chart. I will write more extensively about this in my book in the “Visual Security Analysis” chapter.
What I just learned and what really pointed me to write this blog post is that Excel has a data analysis add-in that lets you compute moving averages. In my Excel instance, I had to first enable the “Data Analysis” add-in by going to Tools|Add-Ins… Once enabled, I got a new menu item under Tools which is Data Analysis… There you can choose from a variety of data analysis tools, among them a moving average calculator. This blog post shows exactly to to apply the add-in.
December 7, 2007
 Finally, Common Event Expression (CEE) has its Web site up!
Finally, Common Event Expression (CEE) has its Web site up!
We are working on a few initiatives right now. If you want to contribute to the discussion, join the mailing list. Send an email to cee@mitre.org to subscribe.
November 14, 2007
 No news anymore, but still worth a blog entry. Michael Rash wrote a new book on firewalls. His approach is not the traditional one where he looks into firewalls themselves. He explores all kinds of additional tools tat can be used alongside of firewalls to tune them and make them more efficient. I have read part of his book before he published it and I really liked what he was up to. I think the final copy should be on my desk by now. Can’t wait to read it. Here is a link to his Web page:
No news anymore, but still worth a blog entry. Michael Rash wrote a new book on firewalls. His approach is not the traditional one where he looks into firewalls themselves. He explores all kinds of additional tools tat can be used alongside of firewalls to tune them and make them more efficient. I have read part of his book before he published it and I really liked what he was up to. I think the final copy should be on my desk by now. Can’t wait to read it. Here is a link to his Web page:
http://www.cipherdyne.org/blog/2007/09/online-site-for-linux-firewalls-attack-detection-and-response.html
October 15, 2007
 I was playing with database audit logs for a bit to try and visualize some aspects of them. While doing so, I came across a pretty interesting problem. The audit logs contain entries that indicate what exact SQL query was executed. Now, I am not interested in the entire query, but I need to know which tables were touched. I was trying to build some regular expressions to extract that information from the query, but I gave up pretty quickly. It’s just too complicated for a regex. I was wondering whether there is a way to take a SQL query, for example:
I was playing with database audit logs for a bit to try and visualize some aspects of them. While doing so, I came across a pretty interesting problem. The audit logs contain entries that indicate what exact SQL query was executed. Now, I am not interested in the entire query, but I need to know which tables were touched. I was trying to build some regular expressions to extract that information from the query, but I gave up pretty quickly. It’s just too complicated for a regex. I was wondering whether there is a way to take a SQL query, for example:
select * from a.table1 a, b.tabl2 b join c.table3 on b.id1=c.id2 where a.foo='bar'
and extract all the table names: a.table1, b.table2, c.table3. Are there tools to do that? Remember, I don’t have the database with these tables. I only have a log from some database. The script should support all the SQL perks like joins, nested selects, etc. Anyone have a good way to do this?
October 4, 2007
 During the FIRST conference in Seville earlier this year, I was talking to Ben Chai at about 12.30am. We were sitting in the bar area when he suddenly took out his microphone and started interviewing me. The talk is pretty funny. The podcast shows that I don’t have a very good sense of humor 😉 Oh, and by the way, reading tea leaves is probably going to be the topic of one of my next talks!
During the FIRST conference in Seville earlier this year, I was talking to Ben Chai at about 12.30am. We were sitting in the bar area when he suddenly took out his microphone and started interviewing me. The talk is pretty funny. The podcast shows that I don’t have a very good sense of humor 😉 Oh, and by the way, reading tea leaves is probably going to be the topic of one of my next talks!
I don’t think this was my best night, when Ben record this. I spend about 1.5 hours trying to pick a TSA lock with a paper clip. Okay, Adam couldn’t do it anymore either, but still. In the meantime, I learned how it is done for real – the lock picking 😉
Listen to the podcast here.
September 24, 2007

I spent the first week of September in Kuala Lumpur, Malaysia, where I was speaking about insider crime visualization at Hack In The Box. The conference is held annually and I was surprised about how big it was. A lot of attendees from the area, but also from other parts of the world, for example from Germany. In general I was fairly impressed with the caliber of people that presented.

What I enjoyed a lot as well, was the lock-picking village … The guys running it were real experts on the topic and had excellent tools to teach you the art of lock picking.
For those interested, I have the presentation available here. The download is fairly big. Sorry about that. The conference also made the rest of the presentations available.
On to the next conference. See you in Jakarta end of October.
September 16, 2007
As you might have seen on secviz.org, AfterGlow 1.5.9 is out. The announcement of AfterGlow 1.5.9 on secviz has some more details on what’s new. Just quickly here: The URL feature is pretty interesting and addresses some old thoughts and things I have been talking about with other people (Peter, are you reading this?). The issue there was that the AfterGlow graphs are very static and that’s kind of a bummer. It would be really nice if there was more interactivity. Clicking on nodes for example. Well, this is now a first step towards that. Along with the Splunk – AfterGlow integration, this is actually going almost all the way of completing the interaction round trip. I know, in terms of real interactivity, there is still a lot missing, but I think this is taking care of some really interesting use-cases.
Technorati Tags: afterglow, visualization, splunk, interactivity, graphviz

 One of the topics I am discussing in the video is the “false dichotomy” between security and visualization. This is a topic that I talked about during a talk at the MIT Lincoln Labs at the beginning of December. The presentation showed how there are really two disciplines that come together in security visualization: Security and Visualization. The problem with this is that visualization people don’t know much about security and the other way around. It’s a very interesting topic to explore and it explains some of the mistakes that are being made with visualization tools and is also reflected in visualization research.
One of the topics I am discussing in the video is the “false dichotomy” between security and visualization. This is a topic that I talked about during a talk at the MIT Lincoln Labs at the beginning of December. The presentation showed how there are really two disciplines that come together in security visualization: Security and Visualization. The problem with this is that visualization people don’t know much about security and the other way around. It’s a very interesting topic to explore and it explains some of the mistakes that are being made with visualization tools and is also reflected in visualization research.

 Today I found myself researching “moving average analysis” techniques. Using moving average analysis can be fairly useful in trending risk. Plot the moving average over your risk and compare it with the actual risk numbers, much like you would analyze a stock chart. I will write more extensively about this in my book in the “Visual Security Analysis” chapter.
Today I found myself researching “moving average analysis” techniques. Using moving average analysis can be fairly useful in trending risk. Plot the moving average over your risk and compare it with the actual risk numbers, much like you would analyze a stock chart. I will write more extensively about this in my book in the “Visual Security Analysis” chapter. Finally,
Finally, 

